Introduction
VPS Domain Forwarding feature in Virtualizor allows VPSes to host HTTP/HTTPS services or any other TCP services on a private IP without any need for a public IP. To host an HTTP/HTTPS service, all that is required for a VPS is a valid domain name registered with any Domain Registrar. This domain name must point to any one of the source IPs made available for VPS Domain Forwarding by Virtualizor administrator.
Terminology
Below is a list of various terms used in this documentation related to VPS Domain Forwarding feature.
- VDF: VPS Domain Forwarding.
- HAProxy service: This is the core service which will be running in background on the server where VPSes are hosted and will be of performing domain forwarding requests for VPSes as per VDF records set.
- Protocol : This is a term related to HAProxy service. Virtualizor uses TCP and HTTP services provided by HAProxy.
- TCP : With this protocol, a VPS can host service which can be accessible through server's Source IPs.
- HTTP/HTTPS : With this protocol, a VPS can host service which can be accessible through Source Domain (Domain Name which VPS user points to any one of Virtualizor server's IP set by Virtualizor Admin).
- Source IP : This is the public IP of the server using which users will be able to access TCP services hosted in VPSes publically.
- Source Domain : This is the domain name through which HTTP/HTTPS services hosted by a VPS can be accessed publically. Source Domain must point to any one of the Source IPs of the server which Virtualizor administrator has made available for VDF. It is the responsiblity of the VPS owner to point VPS domain name to any one of server's Source IP.
- Source Port : This is the port attached to Source IP of the server on which TCP/HTTP/HTTPS service hosted by VPSes will be available publically.
- Destination IP : This is the private (local) IP assigned to VPS on which the VPS will host its services which can be accessed through Source IP and Source Port.
- Destination Port : This is the port attached to Destination IP within VPS on which various services will be listening internally. This services will then be made available publically through HAProxy service.
Configuration
To use Domain Forwarding for VPS, the administrator needs to perform following setup from the Admin Panel:
- Enable HAProxy
- Select and save "Enable HAProxy" option under Admin Panel > Configuration > slave Settings page > HAProxy Settings. This enables Domain Forwarding on master and all its slaves.
- Set HAProxy parameters
- For each Virtualizor hosts (both master and slave), setup following parameters under Admin Panel > Configuraton > Slave Settings page > HAProxy Settings:
- HAProxy Source IPs List of server's IPs which haproxy service can use for VPS Domain Forwarding as source IPs.
- HAProxy Blocked ports List of source ports which will not be allowed for HAProxy.
- HAProxy Allowed Ports for HTTP(S) and TCP List of source ports which can be used by HAProxy service for any service hosted in VPS (TCP, HTTP/HTTPS).
- HAProxy Reserved ports for HTTP and HTTPS only
List of source ports which can be used only for HTTP/HTTPS
services hosted in VPS. These ports must be a subset of allowed ports.
- Notes :
- Multiple IPs must be separated by comma ','. eg: X1.X2.X3.X4,Y1.Y2.Y3.Y4
- Multiple ports must be separated by comma ','. eg: 80,443
- Port ranges can be specified with hyphen '-'. eg: 5020-6020
- Admin can disable Domain Forwarding for individual slaves through Slave Settings
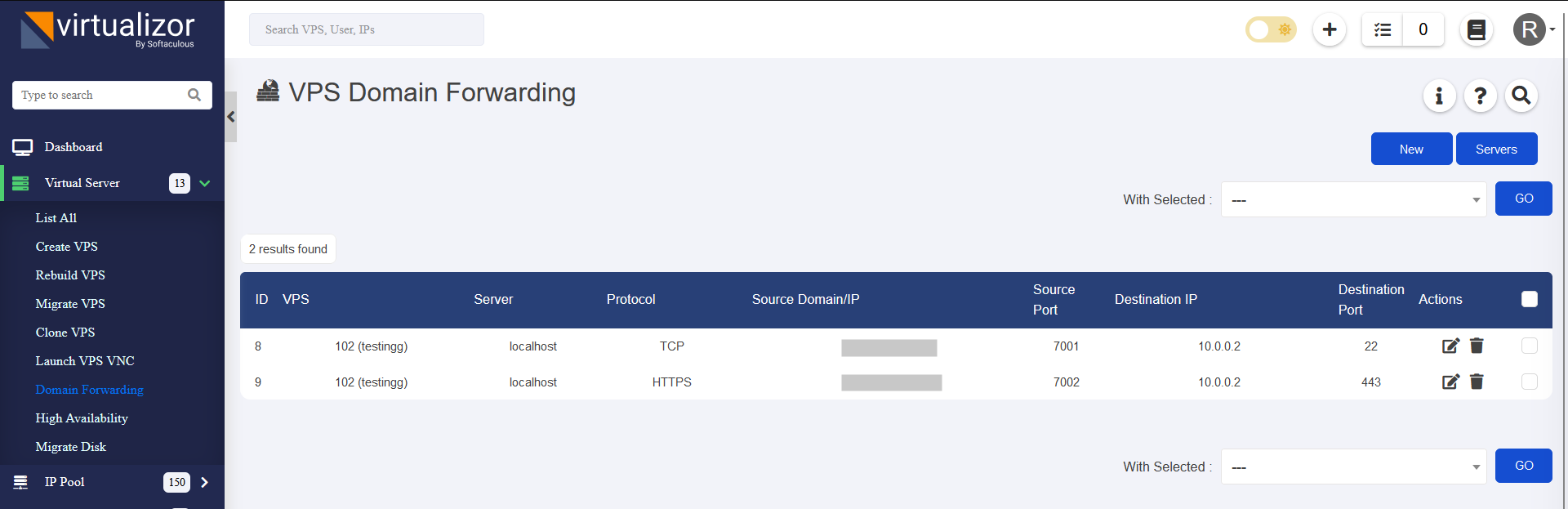
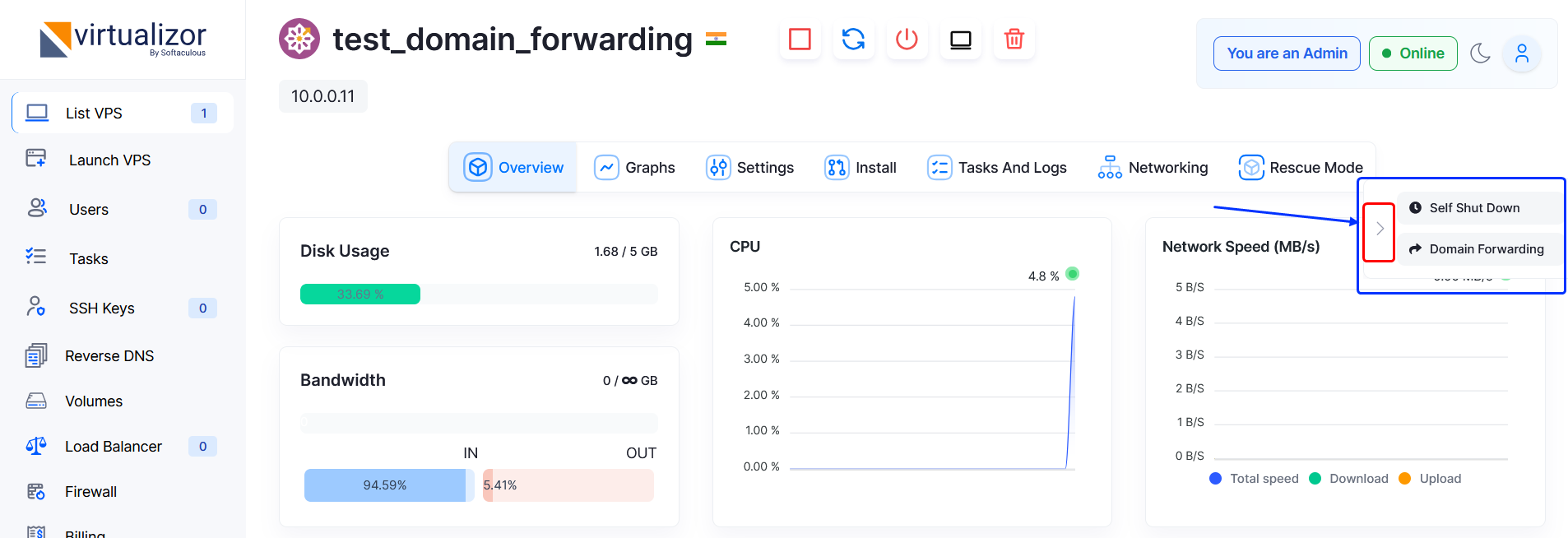
- Admin Panel > Virtual Servers > List All > Select VPS Manage button on right of VPS row > Domain Forwarding
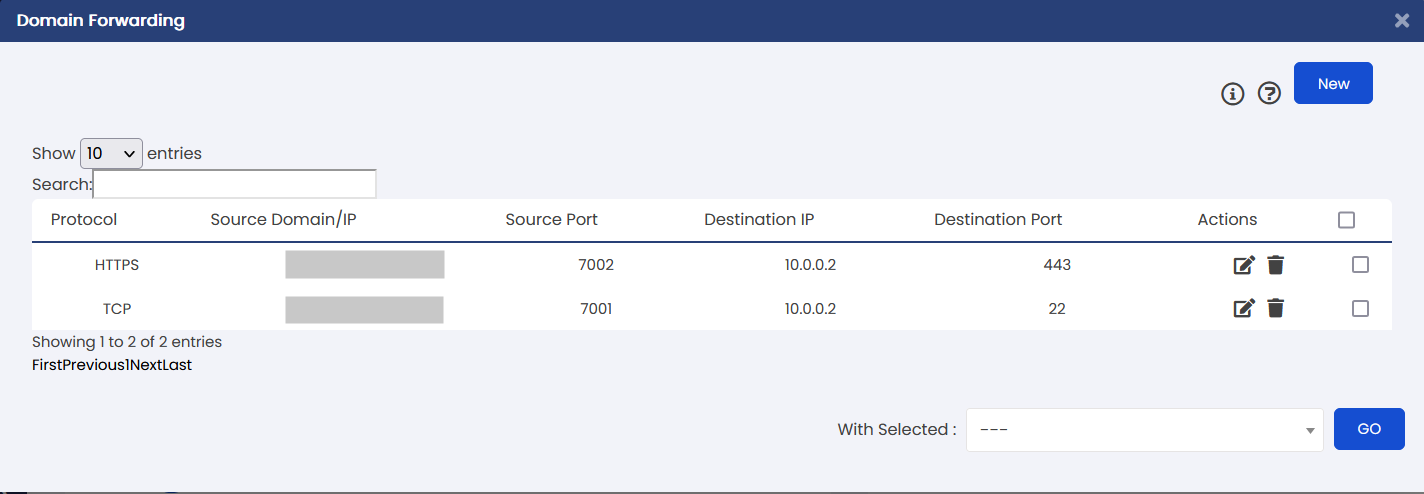
EndUser Panel > VPS Management > Domain Forwarding
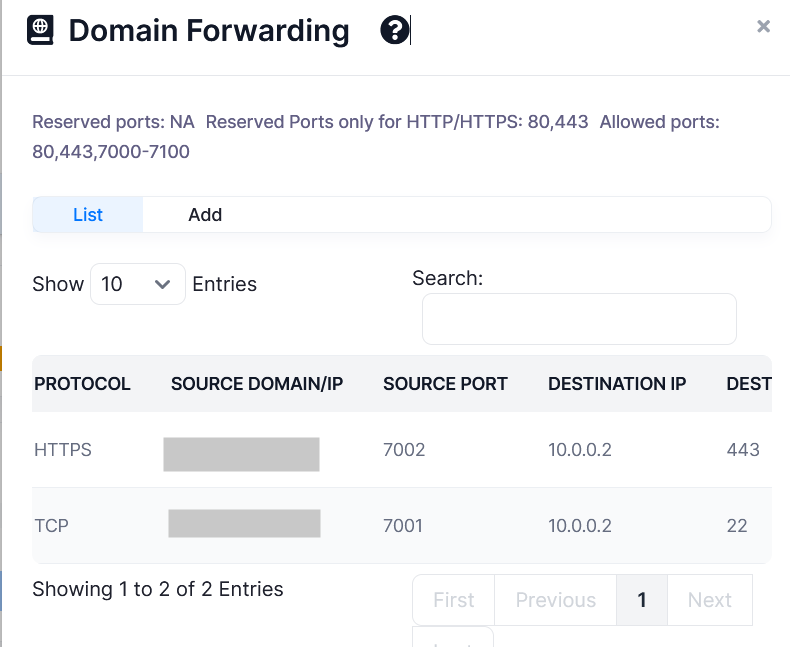
VDF Records table shows following information about records:
- ID: VDF record's unique ID.
- VPS: VPS ID and hostname to which the VDF record belongs [Available only on Admin Panel on Domain Forwarding page]
- Server: Server name of the server on which the VPS is hosted. [Available only on Admin Panel on Domain Forwarding page]
- Protocol: Protocol type of the VDF record.
- Source Domain/IP: Externally visible source domain name or IP of the VDF record through which VPS service will be accessible.
- Source Port: Externally visible source port of the VDF record through which VPS service will be accessible.
- Destination IP: One of the VPS private (local) IPs on which the VPS will be hosting its service internally.
- Destination Port: Port attached to one of the VPS private (local) IPs on which the VPS will be hosting its service internally.
- Actions: Provides the option to udpate/delete VDF record.
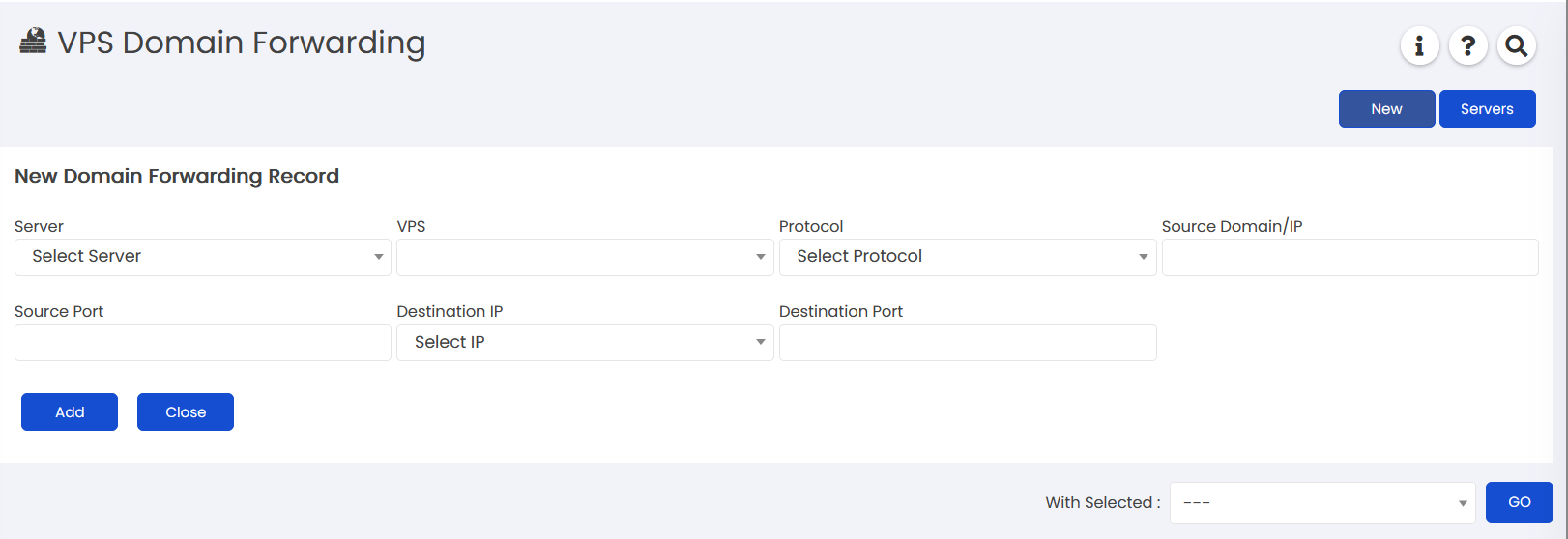
- On Domain Forwarding page, click on "NEW"
- Fill in following details:
- Server: Select the server on which the VPS is hosted. [Available only on Admin Panel on Domain Forwarding page]
- VPS: Select the VPS for which you want to add record. [Available only on Admin Panel on Domain Forwarding page]
- Protocol: Select HTTP or HTTPS protocol for WEB service and TCP for any.
- Source Domain/IP: Select Souce IP if the selected Protocol is TCP. Enter valid domain name if the selected Protocol is HTTP or HTTPS. Note: For HTTP/HTTPS, the domain name must point to one of the server's allowed IP. IP address is not allowed to be used as a Source Domain.
- Source Port: This is the server's port on which it will listen for request from outside (publically).
- Destination IP: One of the IP of the VPS on which to pass on the request internally to the VPS.
- Destination Port: Any port on which the service will be listening on within the VPS.
- Click on "Add" to add the record.
Modifying VDF record

- On Domain Forwarding page, click on edit icon on right of the VDF record.
- Make necessary changes.
- Click on Save icon on the right to save the changes made or revert icon to revert back.
Removing VDF record
- On Domain Forwarding page, click on delete icon on right of the VDF record.
- Confirm to delete.
Removing multiple VDF records
- On Domain Forwarding page, select VDF records which you want to remove.
- At bottom, select "Delete" option and click on "Go".
Note: After VDF record is added, modified or removed, Virtualizor reloads HAProxy service.

It displays:
- ID: Virtualizor server's ID
- Server: Virtualizor server's name
- Enable: Yes/No, HAProxy enabled on this server
- Status: HAProxy service running, stopped, or in error state
- Actions:
Currently two actions are supported: Remap Source IPs: If source IPs have been modified, new IPs can be mapped to already existing old source IPs of the server in HAProxy configuration Reload HAProxy service: When reloading HAProxy service, Virtualizor updates HAProxy configuration with any changes already made and reloads HAProxy service
To view back VDF Records page click on "List Records" button
VPS Migrations
- When VPS is migrated from source to destination, Virtualizor also attempts to migrate that VPSes VDF records after verifying that these records do not conflict with one on destination server.
- Virtualizor allows us to decide whether to stop migration if the records conflict or ignore conflicts and just migrate VPS without migrating VDF records.
- This option can be controled by "Ignore Domain Forwarding if conflict" option on migration page.
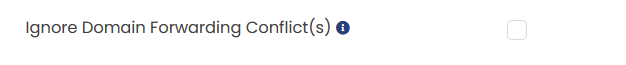
- For multiple VPS migration or VPS clonning, this option is by default ON .
- For single VPS migration, this option is by default OFF, that is, if any conflict occurrs VPS will not be migrated.
Private Network Configurations
NOTE: This will not work on OpenVZ7 or Virtuozzo.
Below we show you example private network configuration on different nodes with specific virtualization.
We will create internal network with following details:
- Network: 10.0.0.0
- Netmask: 255.255.255.0
- Prefix: 24
- Gateway: 10.0.0.1
- Usable IPs: 10.0.0.2 to 10.0.0.50
KVM, LXC, OpenVZ 7 and XEN
For LXC, you will require to install libvirt package manually ( yum install libvirt )
Login to command line console as root and follow below steps on host
where you want internal network with working Internet access:
- Create internal network (eg network and bridge name: HAProxy) on the host
- Navigate to /etc/libvirt/qemu/networks
- Create a new xml file with network_name (eg HAProxy) as filename and with following content:
<network>
<name>HAProxy</name>
<forward mode='nat'/>
<bridge name='HAProxy' stp='on' delay='0' />
<ip address='10.0.0.1' netmask='255.255.255.0'>
</ip>
</network>virsh net-define /etc/libvirt/qemu/networks/HAProxy.xml- Set to auto start this network by running following command (replace network name HAProxy with the one you created in below command):
virsh net-autostart HAProxy- Start this network by running following command (replace network name HAProxy with the one you created in below command):
virsh net-start HAProxy- Now create an IP Pool with internal network details through Virtualizor Admin Panel:
- Navigate to Admin Panel > IP Pool > Create IP Pool
- Select the server where you have setup the internal network
- Provide a meaningful name for this pool
- Set according to our example network:
- Gateway to: 10.0.0.1
- Netmask to: 255.255.255.0
- Nameserver 1: 8.8.8.8
- Nameserver 2: 8.8.4.4
- First IP: 10.0.0.2
- Last IP: 10.0.0.50
- Enable VLAN: checked
- VLAN Bridge: BRIDGE_NAME you set when creating it (HAProxy)
- Click "Add IP Pool" to save the new pool
- Create VPS with any one of the IPs in the above IP range. The VPS will have a working internet access
- Done!
- Create internal network (name: VirtualizorXCPHAProxyNetwork) on the host by running following command:
xe network-create name-label="VirtualizorXCPHAProxyNetwork"- Get the bridge name of this internal network:
xe network-list name-label="VirtualizorXCPHAProxyNetwork" params=bridge- Create a udev rule to run a script once this bridge is updated
- Navigate to path /etc/udev/rules.d/
- Create a file named VirtualizorXCPHAProxyNetwork.rules and add following content:
- Navigate to path /etc/udev/scripts/
- Create a script file named "VirtualizorXCPHAProxyNetwork.sh" to set the bridge IP as gateway IP and netmask mentioned above, for this put following content in this sh file:
bridge=`xe network-list name-label=VirtualizorXCPHAProxyNetwork params=bridge minimal=true`
ifconfig $bridge 10.0.0.1/24
- Make this script file executable by running following command:
- Set the host to forward IPv4 by running following command:
Set the network interface having the public IP in MASQUERADE mode. Assuming xenbr0 is the primary interface with public IP run below command:
- Now create an IP Pool with internal network details through Virtualizor Admin Panel:
- Navigate to Admin Panel > IP Pool > Create IP Pool
- Select the server where you have setup the internal network
- Provide a meaningful name for this pool
- Set according to our example network:
- Gateway to: 10.0.0.1
- Netmask to: 255.255.255.0
- Nameserver 1: 8.8.8.8
- Nameserver 2: 8.8.4.4
- First IP: 10.0.0.2
- Last IP: 10.0.0.50
- Enable VLAN: checked
- VLAN Bridge: xapi0
- Click "Add IP Pool" to save the new pool
- Create VPS with any one of the IPs in the above IP range. The VPS will have a working internet access
- Done!
OpenVZ
- Enable NAT based private networking on OpenVZ if not already enabled by following guide on link: https://openvz.org/Using_NAT_for_container_with_private_IPs
- Set the network interface having the public IP in MASQUERADE mode. Assuming eth0 is the primary interface with public IP, run below command:
- Create an IP Pool with internal network details through Virtualizor Admin Panel:
- Navigate to Admin Panel > IP Pool > Create IP Pool
- Select the server where you want to setup internal network
- Provide a meaningful name for this pool
- Set according to our example network:
- Gateway to: 10.0.0.1
- Netmask to: 255.255.255.0
- Nameserver 1: 8.8.8.8
- Nameserver 2: 8.8.4.4
- First IP: 10.0.0.2
- Last IP: 10.0.0.50
- Click "Add IP Pool" to save the new pool
- Create VPS with any one of the IPs in the above IP range. The VPS will have a working internet access
- Done!
Proxmox
- In case of Proxmox You will need to create a HAProxy Bridge on host server manually by modifiying the network file with iptables NAT rules in it.
- Modify the file : /etc/network/interfaces and create bridge : HAProxy
- In the below example, Server IP is 1.2.3.4 and the internal range with Internet network access is 10.0.0.1/24
iface lo inet loopback
iface ens3 inet manual
#THIS IS DEFAULT BRIDGE FOR PUBLIC NETWORK(EXAMPLE)
auto vmbr0
iface vmbr0 inet static
address 1.2.3.4
netmask 255.255.255.0
gateway 1.2.3.254
bridge_ports ens3
bridge_stp off
bridge_fd 0
#THIS IS HAPROXY BRIDGE WHICH NEEDS TO BE CREATED
auto HAProxy
iface HAProxy inet static
address 10.0.0.1
netmask 255.255.255.0
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.0.0.0/24' -o vmbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.0.0.0/24' -o vmbr0 -j MASQUERADE
#Assuming vmbr0 is server's default network bridge with Public IP.
We are almost setup now. Just make sure everything is correct before you restart the network. After that restart the network :
- Now Create an IP Pool with internal network details through Virtualizor Admin Panel:
- Navigate to Admin Panel > IP Pool > Create IP Pool
- Select the server where you want to setup internal network
- Provide a meaningful name for this pool
- Set according to our example network:
- Gateway to: 10.0.0.1
- Netmask to: 255.255.255.0
- Nameserver 1: 8.8.8.8
- Nameserver 2: 8.8.4.4
- First IP: 10.0.0.2
- Last IP: 10.0.0.50
- Enable VLAN: checked
- VLAN Bridge: HAProxy (As per above example)
- Click “Add IP Pool” to save the new pool
- Create VPS with any one of the IPs in the above IP range. The VPS will have a working internet access
- Done!
